Roles
Roles¶
This section allows you to create roles and associate them with users, to allow or restrict access to different sections of the platform. The access of the roles to the content is defined within the code of each section in the platform itself, so the incorporation of a new role implies the modification of the code to adapt access to information to the capabilities of the new role.
In this section we are initially shown a table similar to those that we can find in other inventories or sections, with pager, filters and other actions already described as global search, by columns, filtering by columns, export, etc.
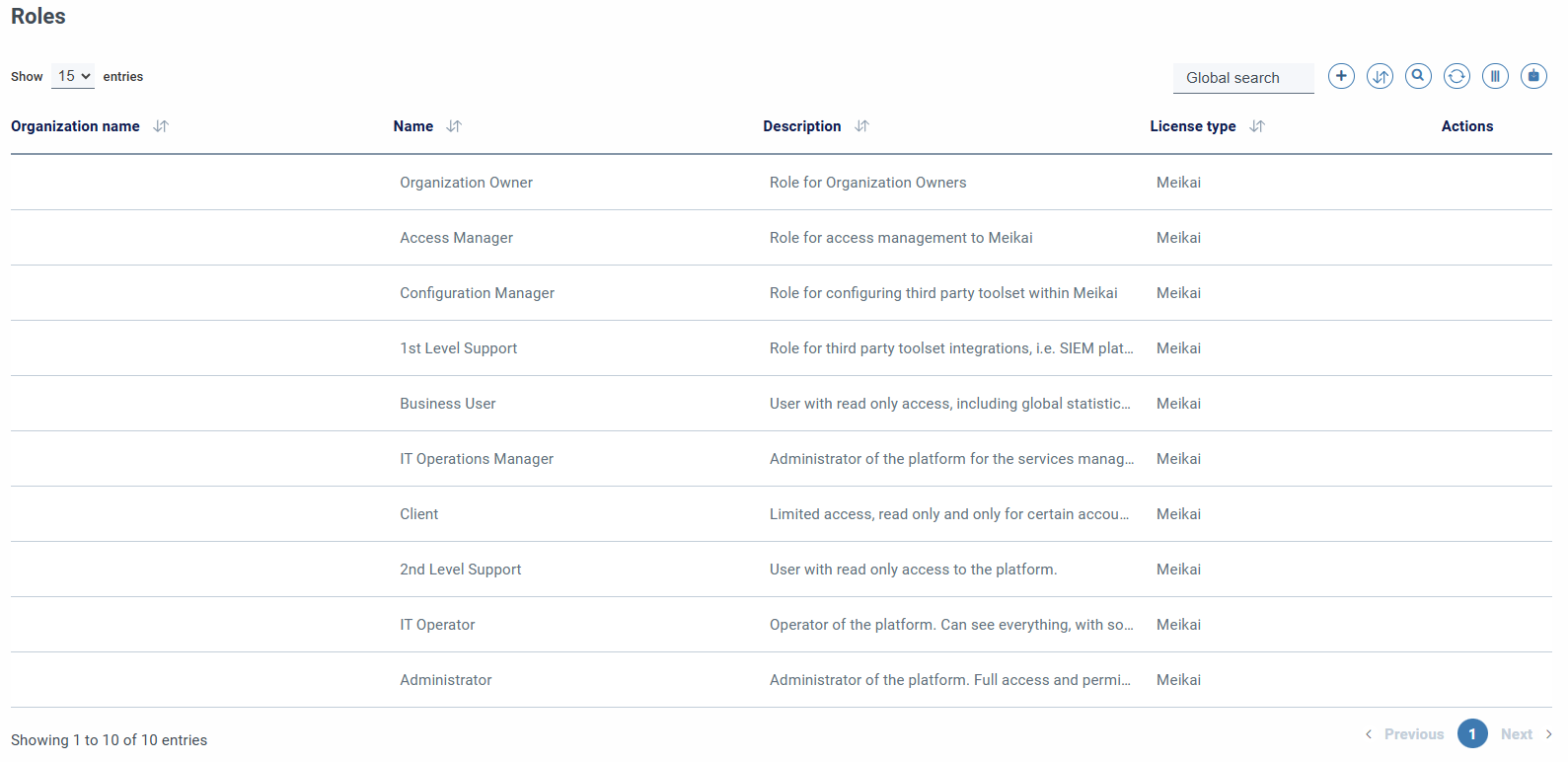
In addition to the options already mentioned, the table actions button incorporates a button to add a new role.
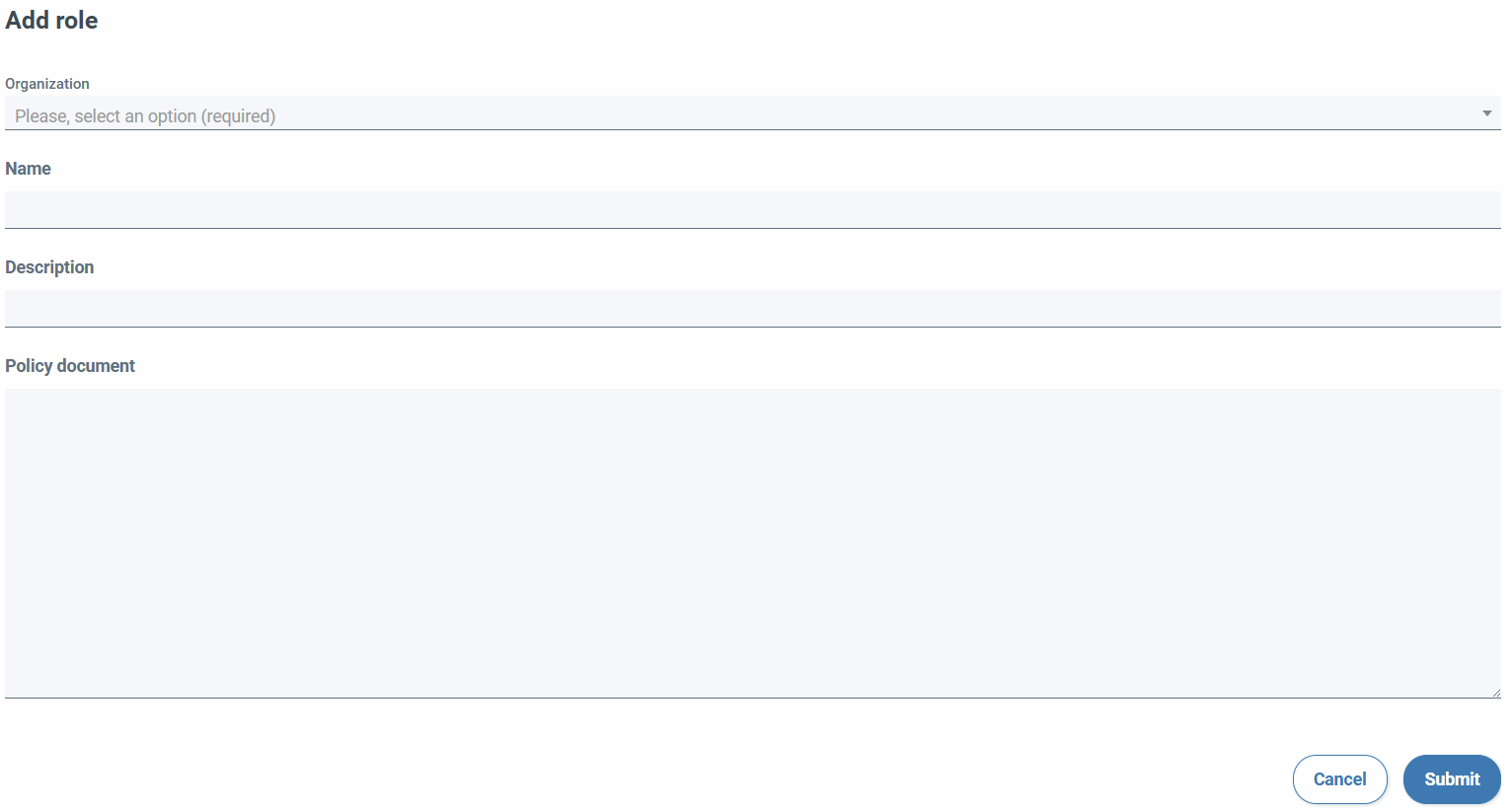
Form fields allow:
- Name the role (required)
- Add a description
In the table we are presented by default the most relevant data for the role, such as:
- Name
- Description
- Actions
Among the actions we find:
- View role
- Edit role
- Delete role
Predefined roles¶
In SSMCM, a series of roles have been defined at a global level that allow you to assign permissions to users and groups without having to create custom roles for a series of basic tasks.
Here are some of the roles:
readonly: Allows read-only access to all application elements (except auditing).admin: It allows you to administer the organization: manage accounts, users, user groups and accounts, etc. But it does not allow you to manage inventory items (off, on, etc.).operator: focused on technicians, it allows you to manage inventory items, scheduler tasks, execute Ansible tasks, etc.auditor: It also allows access to the audit section.
In general, all roles should be used in conjunction with readonly, as the permissions are added.
Policy definition¶
A policy defines whether a user is allowed/denied to perform an action, on a resource, based on a conditions. An example policy document resembles the following:
{
"version": "version, optional",
"name": "name, optional",
"description": "description, optional",
"statements": [
{
"sid": "sid, like a name, optional",
"actions": [
"inventory:describe",
"scheduler:read",
"scheduler:write",
"..."
],
"resources": [
"xxxx",
"yyyy"
],
"conditions": [
{
"op1": "user.name",
"comp": "==",
"op2": "'constant between single quotes'"
},
{
"op1": "user.company.id",
"comp": "==",
"op2": "object.account.company.id"
}
]
}
]
}
- Within a policy it is possible to specify multiple statements.
- Multiple actions can be specified
- Resources are optional; If they are not specified, or some element is indicated as '*', it is assumed that The judgment is enforced for all appeals.
- Conditions are also optional; If specified, they must all be met.
- In one condition, operators are evaluated based on an expression JMESPath on the context of the that the role is evaluated. To specify a constant in any of the operators, you must do between single quotation marks.
The currently supported conditions of comparison are as follows:
=(or==): Make a comparison case-insentitive of the values resulting from the operators.
Note that these roles only apply to accounts or organizations over which the user has permissions; You cannot grant permissions to a user on objects in accounts or organizations from a role over which you do not have permissions.
Examples¶
Allow access to all objects in all inventories:
{
"statements": [
{
"actions": [
"inventory:describe"
]
}
]
}
Allow actions to all objects in all inventories in DEV and PRE environments:
{
"statements": [
{
"actions": [
"inventory:actions"
],
"conditions": [
{
"op1": "object.environment_tag",
"comp": "==",
"op2": "'DEV'"
}
]
},
{
"actions": [
"inventory:actions"
],
"conditions": [
{
"op1": "object.environment_tag",
"comp": "==",
"op2": "'PRE'"
}
]
}
]
}
Allow actions to be performed on inventory items whose 'resource_group' (Azure) matches the identifier User:
{
"statements": [
{
"actions": [
"inventory:actions"
],
"conditions": [
{
"op1": "object.resource_group",
"comp": "==",
"op2": "user.username"
}
]
}
]
}
List of available actions¶
AccountContacts:ACCOUNT_CONTACT_READ_PERMISSION(accountcontact:read)ACCOUNT_CONTACT_WRITE_PERMISSION(accountcontact:write)
AccountGroups:ACCOUNTGROUP_READ_PERMISSION(accountgroup:read)ACCOUNTGROUP_WRITE_PERMISSION(accountgroup:write)
Accounts:ACCOUNT_READ_PERMISSION(account:read)ACCOUNT_WRITE_PERMISSION(account:write)ACCOUNT_DELETE_PERMISSION(account:delete)ACCOUNT_INVENTORY_PERMISSION(account:inventory)ACCOUNT_BACKUP_PERMISSION(account:backup)
Ansible:ANSIBLE_READ_PERMISSION(ansible:read)ANSIBLE_EXECUTE_PERMISSION(ansible:execute)
AuditMessages:AUDIT_READ_PERMISSION(audit:read)
AzureClients:AZURECLIENT_READ_PERMISSION(azureclient:read)AZURECLIENT_WRITE_PERMISSION(azureclient:write)
AzureTenants:AZURETENANT_READ_PERMISSION(azuretenant:read)AZURETENANT_WRITE_PERMISSION(azuretenant:write)
BackupCleanLogs:CLEANLOG_READ_PERMISSION(cleanlog:read)
BackupLogs:BACKUPLOG_READ_PERMISSION(backuplog:read)
BaseInventories:INVENTORY_READ_PERMISSION(inventory:read)INVENTORY_ACTIONS_PERMISSION(inventory:actions)
CloudMaintenances:CLOUD_MAINTENANCES_READ_PERMISSION(cloudmaintenances:read)
CloudProviderAlerts:CLOUD_PROVIDER_ALERTS_READ_PERMISSION(cloudprovideralert:read)
Compliance:COMPLIANCE_READ_PERMISSION(compliance:read)
Contacts:CONTACT_READ_PERMISSION(contact:read)CONTACT_WRITE_PERMISSION(contact:write)
Credentials:CREDENTIAL_READ_PERMISSION(credential:read)CREDENTIAL_WRITE_PERMISSION(credential:write)
GlobalApiKeys:GLOBALAPIKEY_READ_PERMISSION(globalapikey:read)GLOBALAPIKEY_WRITE_PERMISSION(globalapikey:write)
IssueManagerTickets:TICKETS_READ_PERMISSION(ticket:read)
IssueTrackers:TICKETING_MANAGER_READ(ticketingmanager:read)TICKETING_MANAGER_WRITE(ticketingmanager:write)
Maintenance:MAINTENANCE_CLEARCACHE_PERMISSION(maintenance:clear_cache): Clear application cacheMAINTENANCE_DISCOVERAWSACCCOUNTS_PERMISSION(maintenance:discover_aws_accounts): Launch AWS accounts discovery processMAINTENANCE_DISCOVERAZUREACCCOUNTS_PERMISSION(maintenance:discover_azure_accounts): Launch Azure subscriptions discovery processMAINTENANCE_DISCOVERGCLOUDACCCOUNTS_PERMISSION(maintenance:discover_gcloud_accounts): Launch Google Cloud projects discovery processMAINTENANCE_SYNCSCHEDULERTASKS_PERMISSION(maintenance:sync_scheduler_tasks): Launch scheduler tasks synchronization processMAINTENANCE_UPDATEISSUES_PERMISSION(maintenance:update_issues): Launch issue tickets synchronization processMAINTENANCE_UPDATEMONITORING_PERMISSION(maintenance:update_monitoring): Launch monitoring alerts synchronization process
Monitoring:MONITORING_READ_PERMISSION(monitoringalert:read)
MonitoringManagers:MONITORINGMANAGER_READ_PERMISSION(monitoringmanager:read)MONITORINGMANAGER_WRITE_PERMISSION(monitoringmanager:write)
Organizations:ORGANIZATION_READ_PERMISSION(organization:read)ORGANIZATION_WRITE_PERMISSION(organization:write)
Roles:ROLE_READ_PERMISSION(role:read)ROLE_WRITE_PERMISSION(role:write)
Schedulers:SCHEDULER_READ_PERMISSION(scheduler:read)SCHEDULER_WRITE_PERMISSION(scheduler:write)SCHEDULER_EXECUTE_PERMISSION(scheduler:execute)
ServiceUpdateStatus:UPDATER_STATUS_READ_PERMISSION(updaterstatus:read)UPDATER_STATUS_EXECUTE_PERMISSION(updaterstatus:execute)UPDATER_STATUS_DELETE_PERMISSION(updaterstatus:delete)
Stats:STATS_READ_PERMISSION(stats:read)
Trends:TRENDS_READ_PERMISSION(trends:read)
Users:USER_READ_PERMISSION(user:read)USER_WRITE_PERMISSION(user:write)