Google Cloud
Google Cloud¶
One of the providers supported by SSMCM is Google Cloud. To integrate Google Cloud projects into SSMCM, we will have to give permissions to the SSMCM Service Account:
To do this, we can do it in two different ways:
- At the organizational level, if our projects belong to an organization and we want to give access to all the projects of the same.
- At the project level individually.
The steps to be performed are as follows, whether it is done at the organization or project level:
- Create the CompassRole custom role
- Set permissions
- Enable APIs
With these steps done, SSMCM will automatically detect the new Google Cloud projects on which it has permissions and import them as new accounts. After discovering them, the inventory will be carried out automatically.
Step 1: Create the CompassRole role¶
One of the previous steps for configuring the organization or projects so that they can be used by SSMCM, is to create a custom role for shutting down, powering, backup, etc. of the elements.
To do this, we have 2 options:
- Create this role at the organization level, so that permissions can be given at the entire organization level or to child projects
- create this role at the level of each project, so it would be necessary to create the role in each project and give permissions to each project
Creating the role at the organization level¶
Having selected the corresponding organization in the project selector, we will go to the "IAM & admin" section and then to "Roles"; click on "Create Role". The next screen should be as follows, and press the "Create" button:
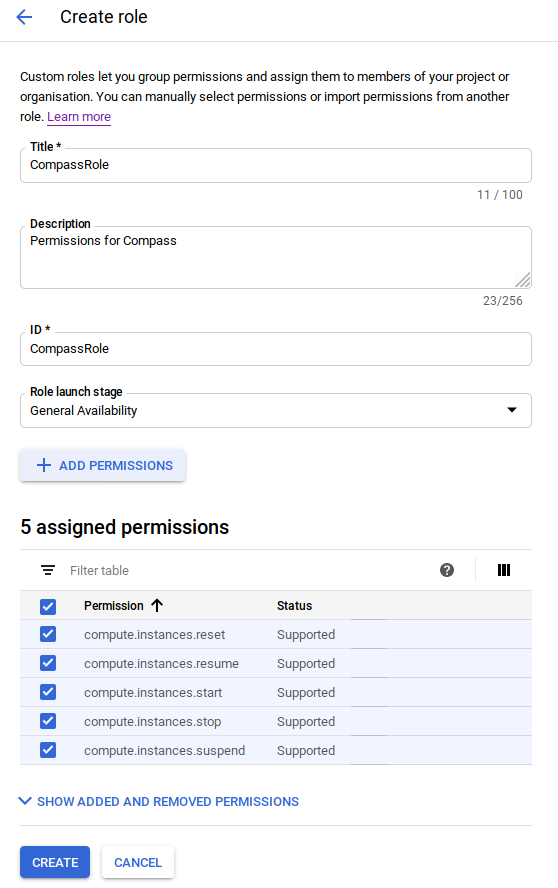
It is also possible to perform this step through the CLI, replacing ORGANIZATION_ID with the corresponding organization number (it can be consulted in the section "IAM & admin" → "Settings"):
ORG_ID=ORGANIZATION_ID
if ! gcloud iam roles describe CompassRole --organization ${ORG_ID} --format none 2> /dev/null ; then
echo "Organization ${ORG_ID}: Creating role CompassRole..."
gcloud iam roles create CompassRole --organization ${ORG_ID} \
--title CompassRole --description "Permissions for SSMCM" \
--stage GA
fi
if [[ "$(gcloud iam roles describe --organization ${ORG_ID} CompassRole --format "value(deleted)")" == "True" ]]; then
echo "Organization ${ORG_ID}: Undeleting role CompassRole..."
gcloud iam roles undelete CompassRole --organization ${ORG_ID} --format none
fi
echo "Organization ${ORG_ID}: Updating permissions of role CompassRole..."
gcloud iam roles update CompassRole --organization ${ORG_ID} \
--title CompassRole --description "Permissions for SSMCM" \
--stage GA --permissions compute.instances.start,compute.instances.stop,compute.instances.suspend,compute.instances.resume,compute.instances.reset --format none
Project-level role creation¶
Having selected the corresponding project in the project selector, we will go to the "IAM & admin" section and then to "Roles"; click on "Create Role". The next screen should be as follows, and press the "Create" button:

It is also possible to perform this step through the CLI:
if ! gcloud iam roles describe CompassRole --project ${GOOGLE_CLOUD_PROJECT} --format none 2> /dev/null ; then
echo "Project: ${GOOGLE_CLOUD_PROJECT}: Creating role CompassRole..."
gcloud iam roles create CompassRole --project ${GOOGLE_CLOUD_PROJECT} \
--title CompassRole --description "Permissions for SSMCM" \
--stage GA
fi
if [[ "$(gcloud iam roles describe --project ${GOOGLE_CLOUD_PROJECT} CompassRole --format "value(deleted)")" == "True" ]]; then
echo "Project: ${GOOGLE_CLOUD_PROJECT}: Undeleting role CompassRole..."
gcloud iam roles undelete CompassRole --project ${GOOGLE_CLOUD_PROJECT} --format none
fi
echo "Project: ${GOOGLE_CLOUD_PROJECT}: Updating permissions of role CompassRole..."
gcloud iam roles update CompassRole --project ${GOOGLE_CLOUD_PROJECT} \
--title CompassRole --description "Permissions for SSMCM" \
--stage GA --permissions compute.instances.start,compute.instances.stop,compute.instances.suspend,compute.instances.resume,compute.instances.reset --format none
Info
The variable GOOGLE_CLOUD_PROJECT is automatically set in the Cloud Shell console; if running from another type of console, you must manually set this variable, the value of which is the ID of the project on which permissions are being given.
Step 2: Set permissions¶
Now we must add permissions to the SSMCM service account. As in the previous step, we will be able to do this both at the organization level and at the project level.
Set organization-level permissions¶
By setting permissions at the organization level, we will make SSMCM able to access all projects under that organization. To do this, having selected the corresponding organization in the project selector, we will go to the "IAM & admin" section and then to "IAM"; click on "Add". We will select the following values:
- New members: ssmcm-connnector@pv2n882n59ls.iam.gserviceaccount.com
- Select a role: Project → Viewer
- Select a role: Organization → Viewer
- Add another role, clicking on "Add another role", and select "CompassRole"
- Click on "Save"
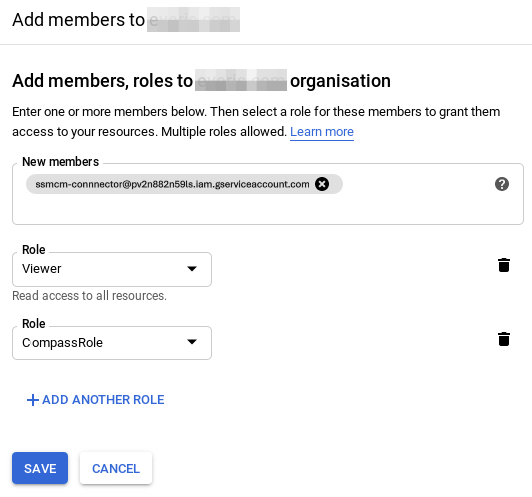
It is also possible to perform this step through the CLI, replacing ORGANIZATION_ID with the corresponding organization number (it can be consulted in the section "IAM & admin" → "Settings"):
ORG_ID=ORGANIZATION_ID
gcloud organizations add-iam-policy-binding ${ORG_ID} \
--member serviceAccount:ssmcm-connnector@pv2n882n59ls.iam.gserviceaccount.com \
--role roles/viewer
gcloud organizations add-iam-policy-binding ${ORG_ID} \
--member serviceAccount:ssmcm-connnector@pv2n882n59ls.iam.gserviceaccount.com \
--role organizations/ORGANIZATION_ID/roles/CompassRole
Set project-level permissions¶
Having selected the corresponding project in the project selector, we will go to the "IAM & admin" section and then to "IAM"; click on "Add". . We will select the following values:
- New members: ssmcm-connnector@pv2n882n59ls.iam.gserviceaccount.com
- Select a role: Project → Viewer
- Add another role, clicking on "Add another role", and select "CompassRole"
- Click on "Save"
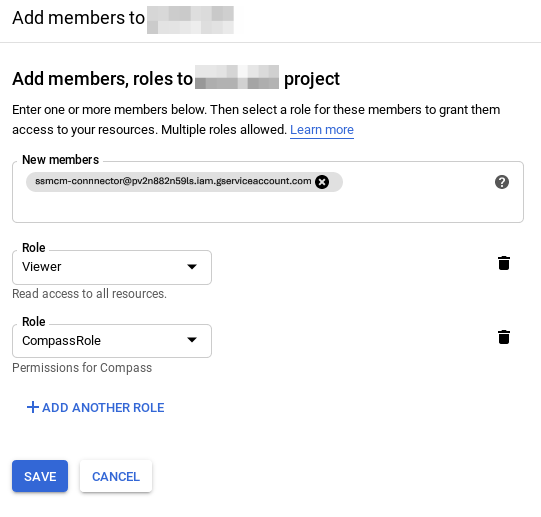
It is also possible to perform this step through the CLI:
gcloud projects add-iam-policy-binding ${GOOGLE_CLOUD_PROJECT} \
--member serviceAccount:ssmcm-connnector@pv2n882n59ls.iam.gserviceaccount.com \
--role roles/viewer
gcloud projects add-iam-policy-binding ${GOOGLE_CLOUD_PROJECT} \
--member serviceAccount:ssmcm-connnector@pv2n882n59ls.iam.gserviceaccount.com \
--role projects/${GOOGLE_CLOUD_PROJECT}/roles/CompassRole
Info
The variable GOOGLE_CLOUD_PROJECT is automatically set in the Cloud Shell console; if running from another type of console, you must manually set this variable, the value of which is the ID of the project on which permissions are being given.
Step 3: Enabling APIs¶
Finally, it is necessary to enable the APIs for each project.
Notice
This step cannot be performed at the organizational level, but will need to be done for each project.
To enable APIs from the web console, follow these steps:
- Select "APIs & Services" in the side menu
- Click on "Enable APIs and services"
- Search for "Google Cloud DNS API"
- If the API is not enabled, click on "Enable"
- Repeat steps 3 and 4 with the following APIs:
- Compute Engine API
- Cloud Spanner API
- Service Health API
- Security Command Center API
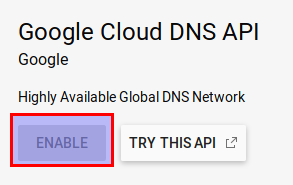
You can also perform these steps from the CLI:
for API in dns.googleapis.com compute.googleapis.com spanner.googleapis.com servicehealth.googleapis.com securitycenter.googleapis.com; do
echo "Project: ${GOOGLE_CLOUD_PROJECT}: Enabling API ${API}..."
gcloud services enable --project ${GOOGLE_CLOUD_PROJECT} ${API}
done
Info
The variable GOOGLE_CLOUD_PROJECT sand automatically set in the Cloud Shell console; if running from another type of console, you must manually set this variable, the value of which is the ID of the project on which permissions are being given.
You can also enable APIs on all projects in your organization by running the following block of code from the CLI:
for PROJECT in $(gcloud projects list --format "value(projectId)") ; do
for API in dns.googleapis.com compute.googleapis.com spanner.googleapis.com servicehealth.googleapis.com securitycenter.googleapis.com; do
echo "Project: ${PROJECT}: Enabling API ${API}..."
gcloud services enable --project ${PROJECT} ${API}
done
done
Audit role¶
The process for creating the audit role is very similar to step Step 2: Set permissions, we will follow the following steps, whether it is done at the organization or project level.
We will add read-only permissions to the SSMCM service account; We will be able to do this both at the organizational level and at the project level.
Set organization-level permissions¶
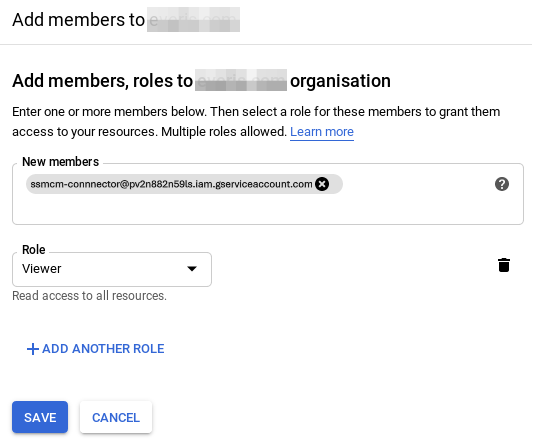
By setting permissions at the organization level, we will make SSMCM able to access all projects under that organization. To do this, having selected the corresponding organization in the project selector, we will go to the "IAM & admin" section and then to "IAM"; click on "Add". We will select the following values:
- New members: ssmcm-connnector@pv2n882n59ls.iam.gserviceaccount.com
- Select a role: Project → Viewer
- Click on "Save"
It is also possible to perform this step through the CLI, replacing ORGANIZATION_ID with the corresponding organization number (it can be consulted in the section "IAM & admin" → "Settings"):
ORG_ID=ORGANIZATION_ID
gcloud organizations add-iam-policy-binding ${ORG_ID} \
--member serviceAccount:ssmcm-connnector@pv2n882n59ls.iam.gserviceaccount.com \
--role roles/viewer
Set project-level permissions¶
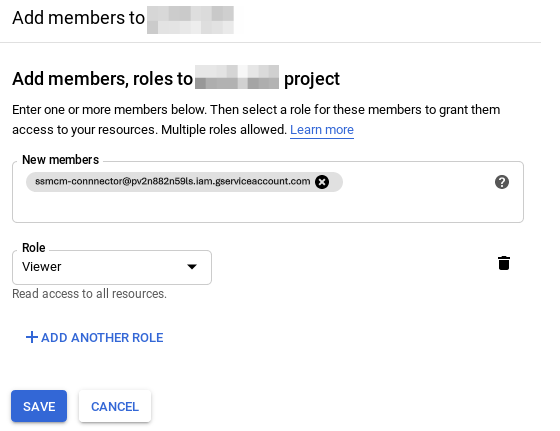
Having selected the corresponding project in the project selector, we will go to the "IAM & admin" section and then to "IAM"; click on "Add". We will select the following values:
- New members: ssmcm-connnector@pv2n882n59ls.iam.gserviceaccount.com
- Select a role: Project → Viewer
- Click on "Save"
It is also possible to perform this step through the CLI:
gcloud projects add-iam-policy-binding ${GOOGLE_CLOUD_PROJECT} \
--member serviceAccount:ssmcm-connnector@pv2n882n59ls.iam.gserviceaccount.com \
--role roles/viewer
Info
The variable GOOGLE_CLOUD_PROJECT is automatically set in the Cloud Shell console; if running from another type of console, you must manually set this variable, the value of which is the ID of the project on which permissions are being given.